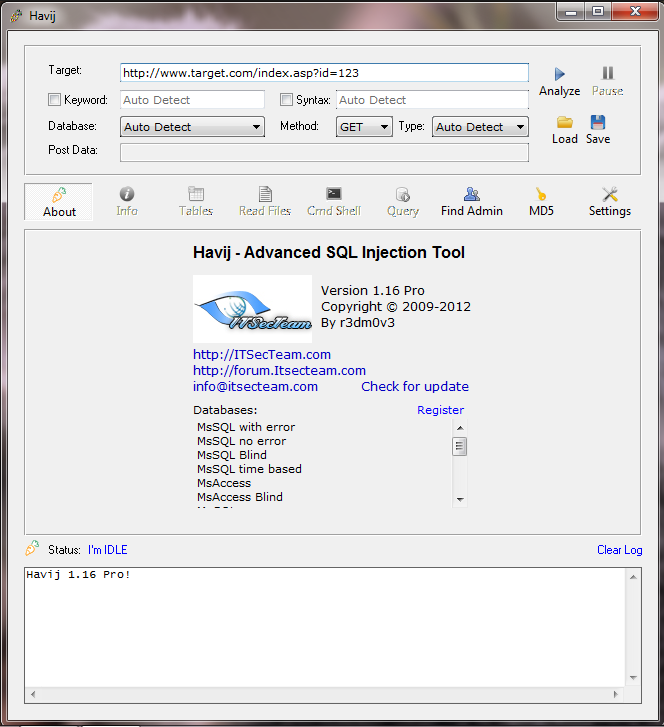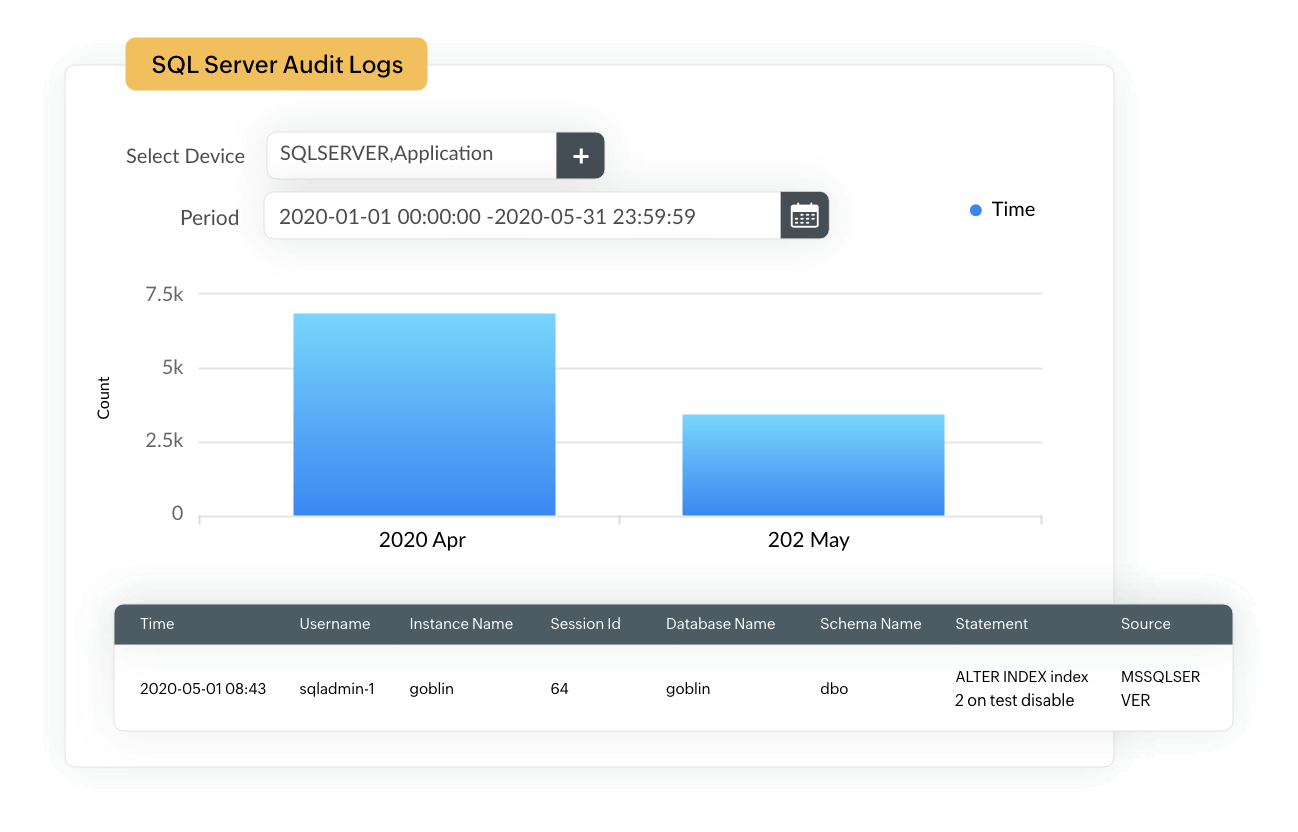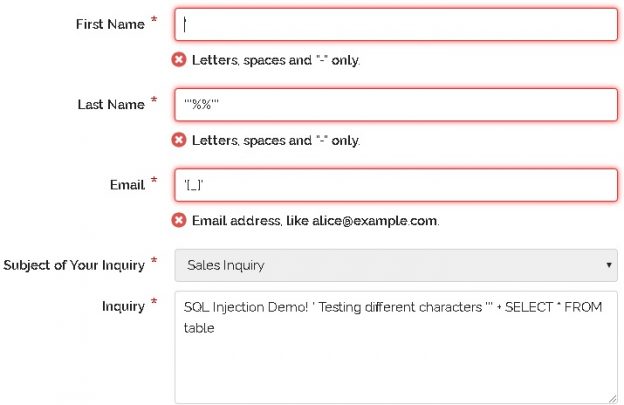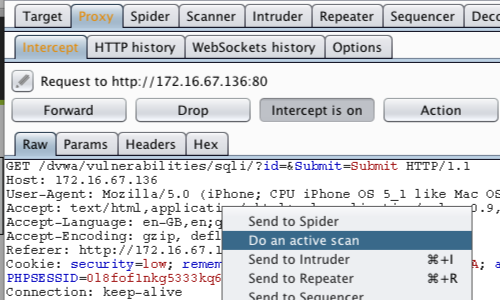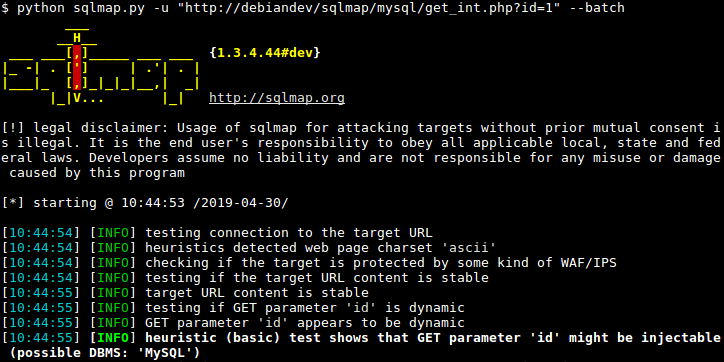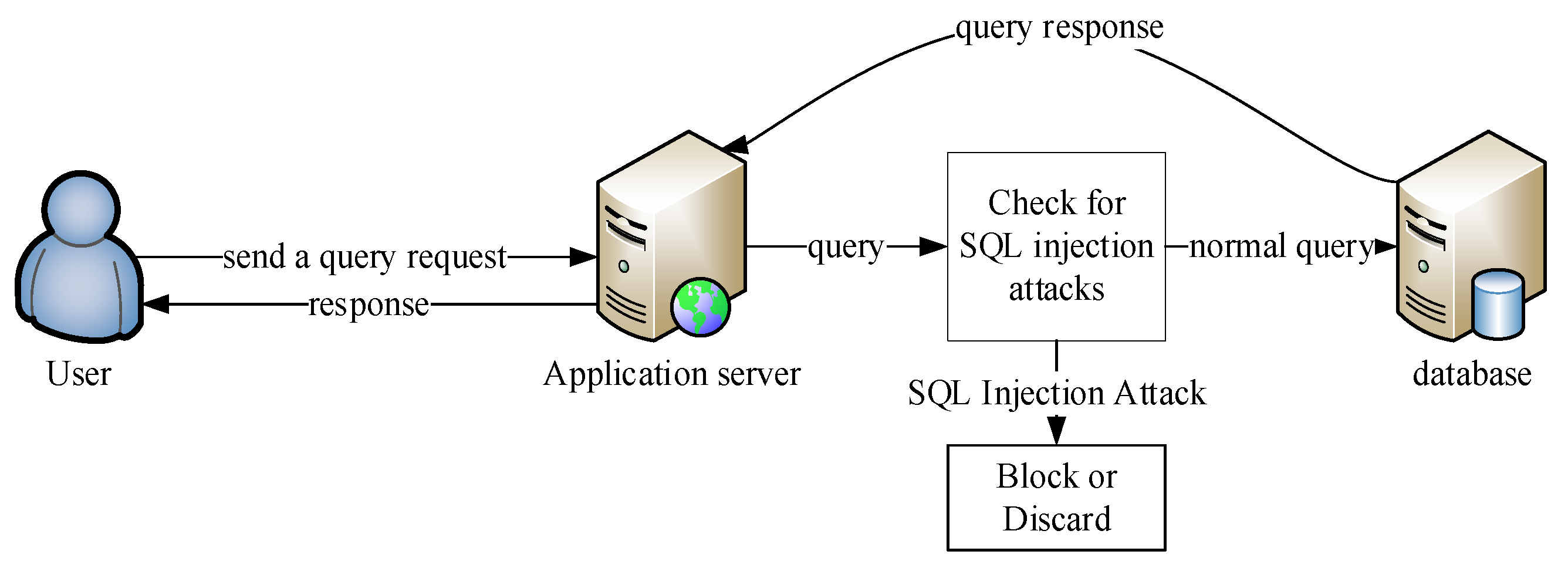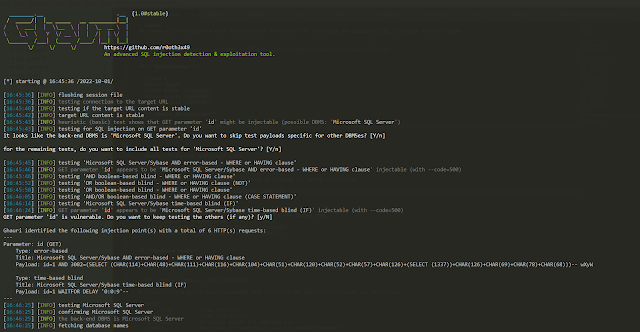
Ghauri - An Advanced Cross-Platform Tool That Automates The Process Of Detecting And Exploiting SQL Injection Security Flaws
![PDF] Comparison of SQL Injection Detection and Prevention Tools based on Attack Type and Deployment Requirements | Semantic Scholar PDF] Comparison of SQL Injection Detection and Prevention Tools based on Attack Type and Deployment Requirements | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a7e46de3d021076f01e62cdd839e20be9192f287/4-Table1-1.png)
PDF] Comparison of SQL Injection Detection and Prevention Tools based on Attack Type and Deployment Requirements | Semantic Scholar
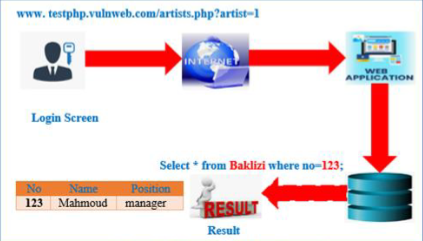
A Technical Review of SQL Injection Tools and Methods: A Case Study of SQLMap | International Journal of Intelligent Systems and Applications in Engineering


![PDF] SQL Injection detection using machine learning | Semantic Scholar PDF] SQL Injection detection using machine learning | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/04f57005444ca5c066df57887da1b2147e681e52/3-Figure1-1.png)