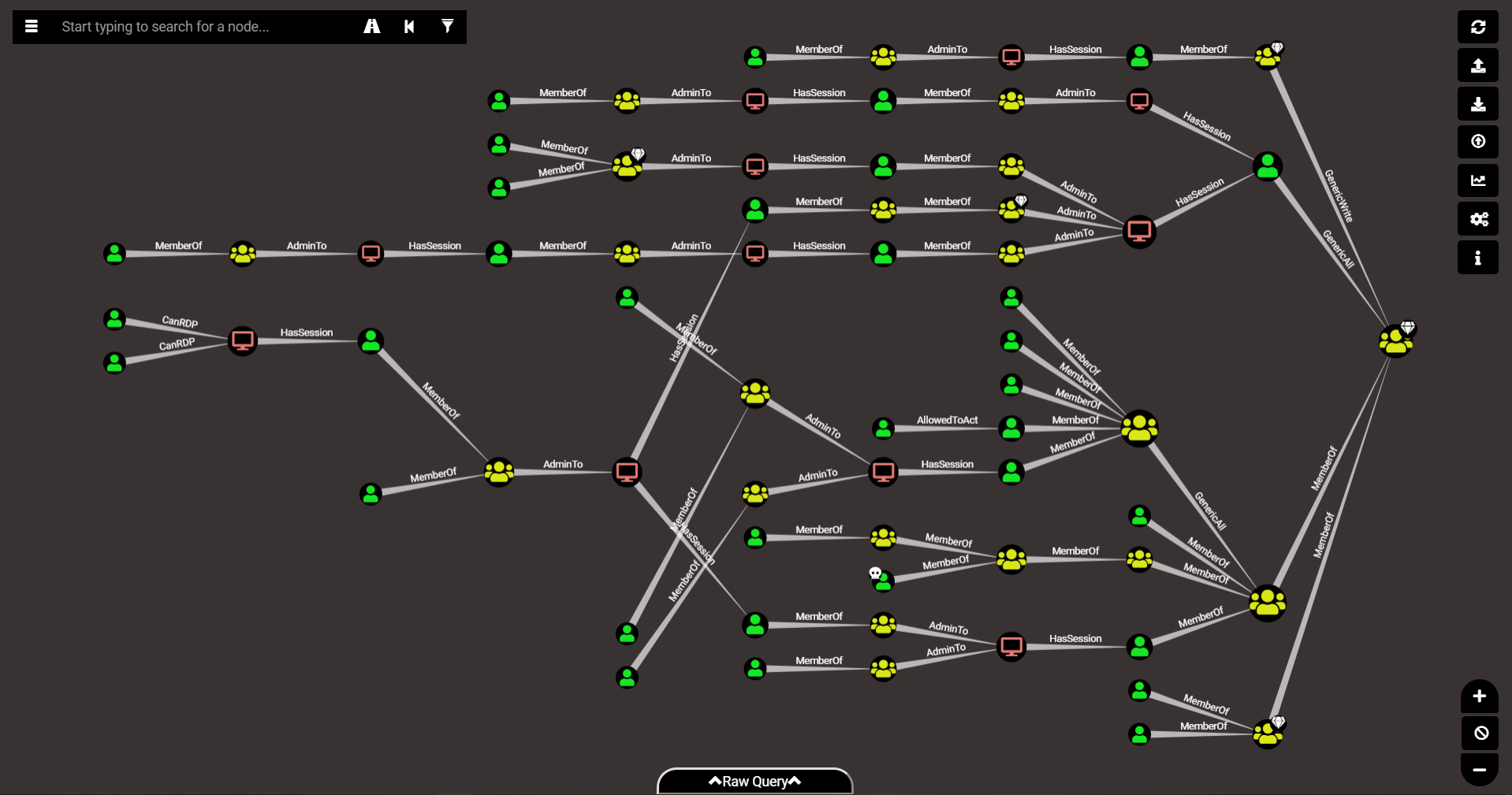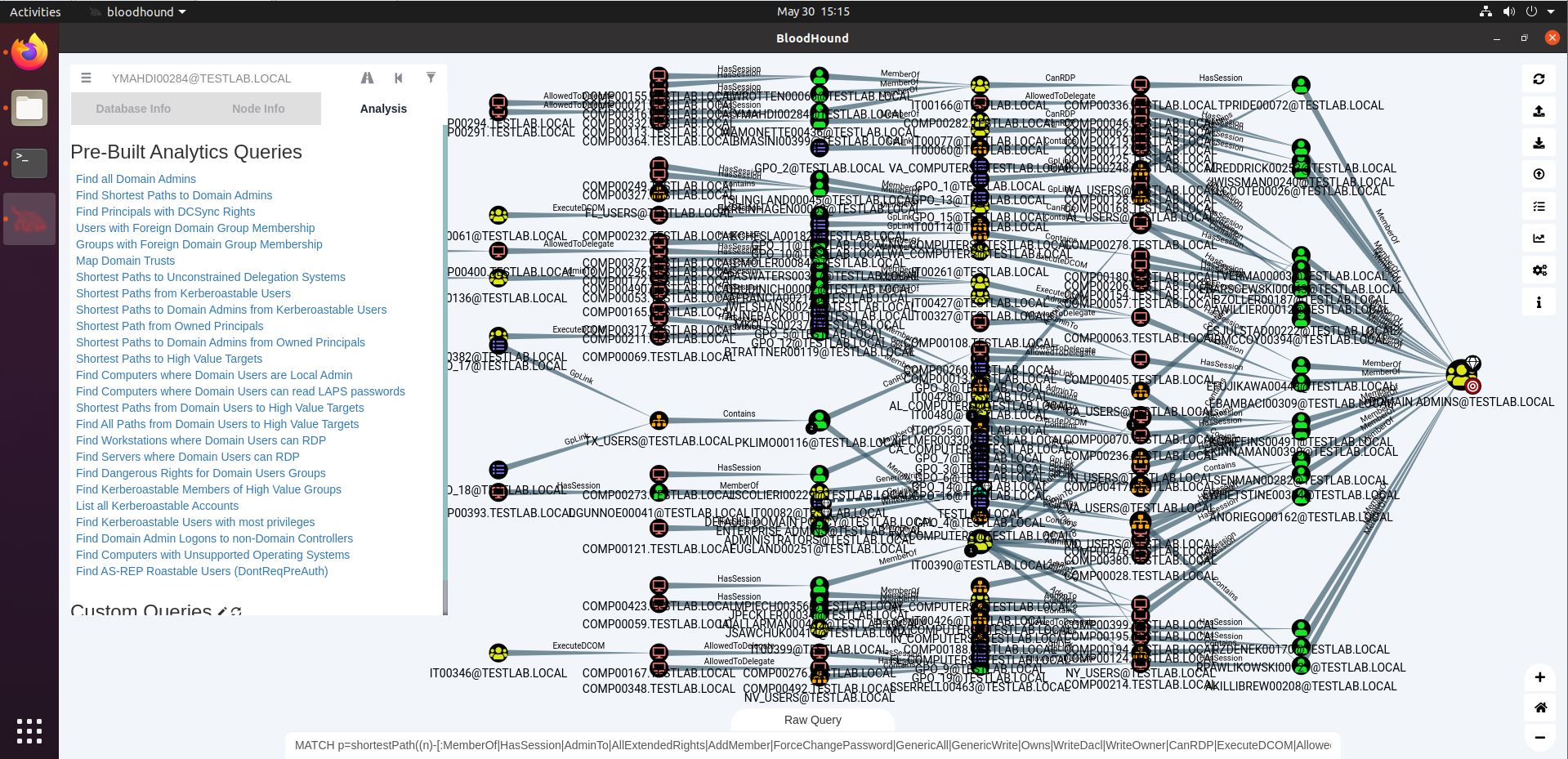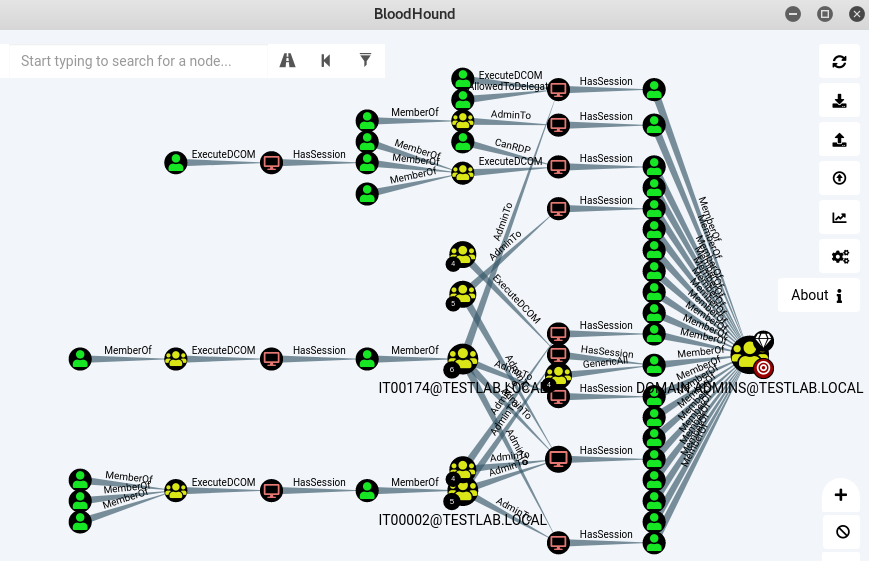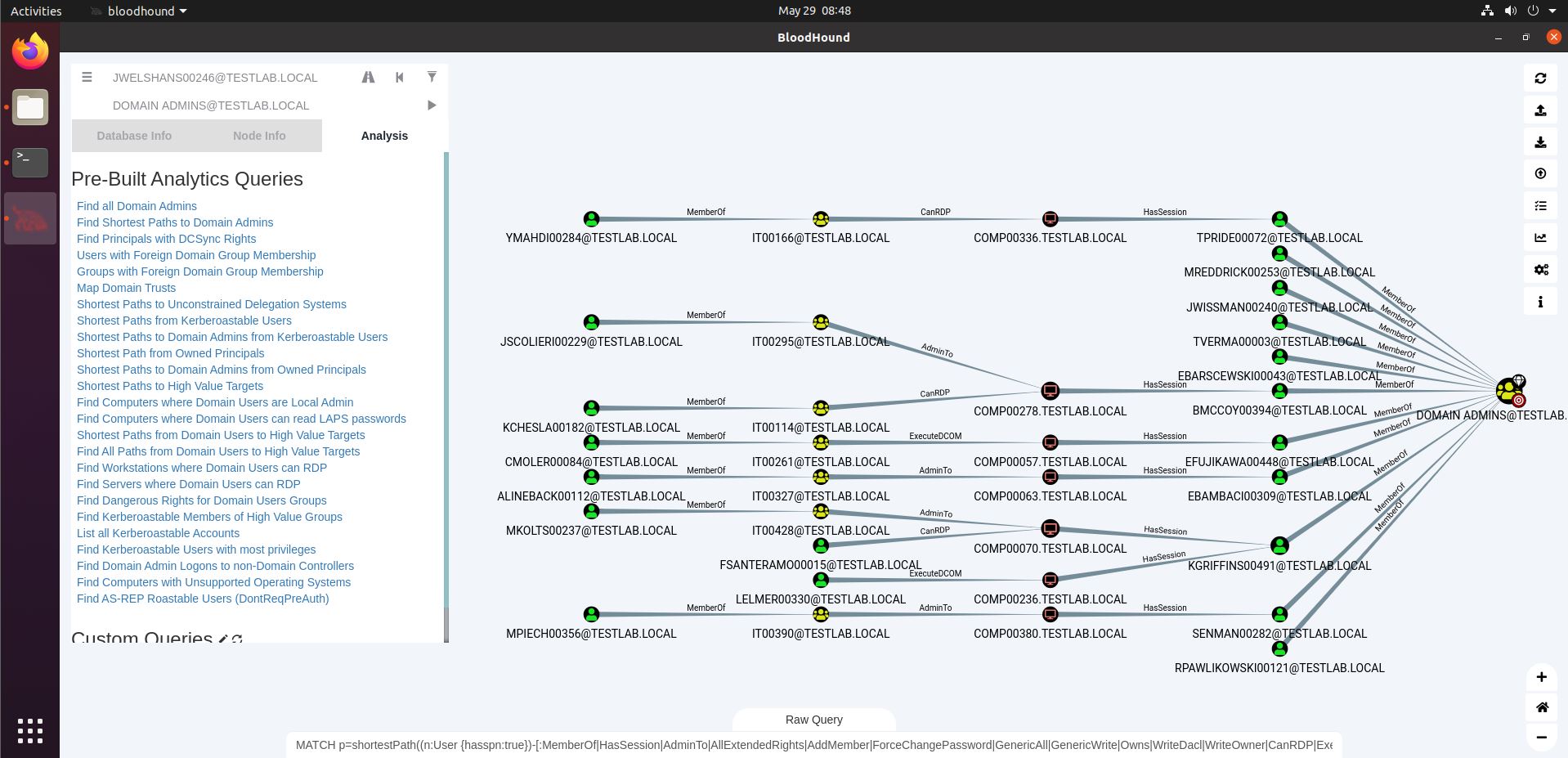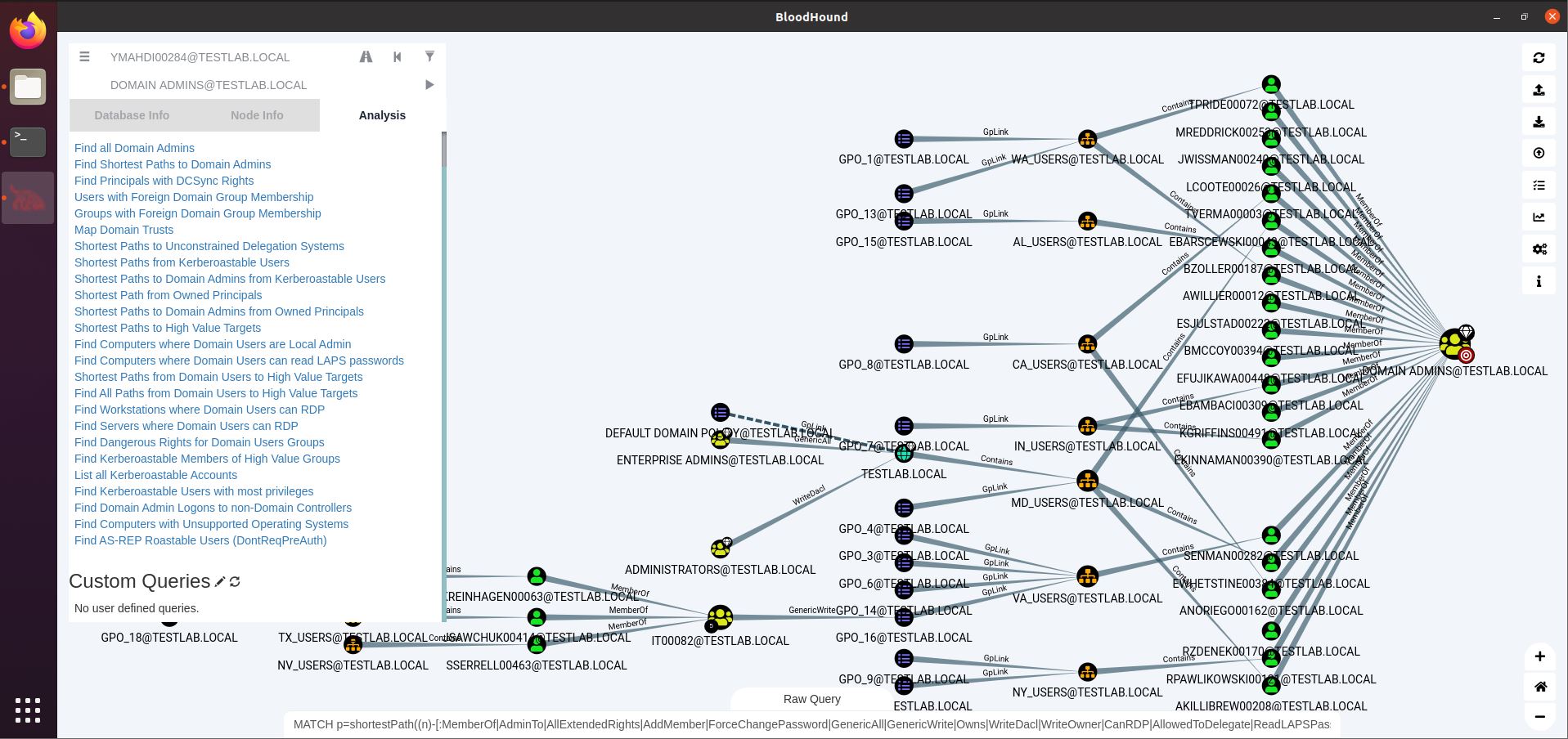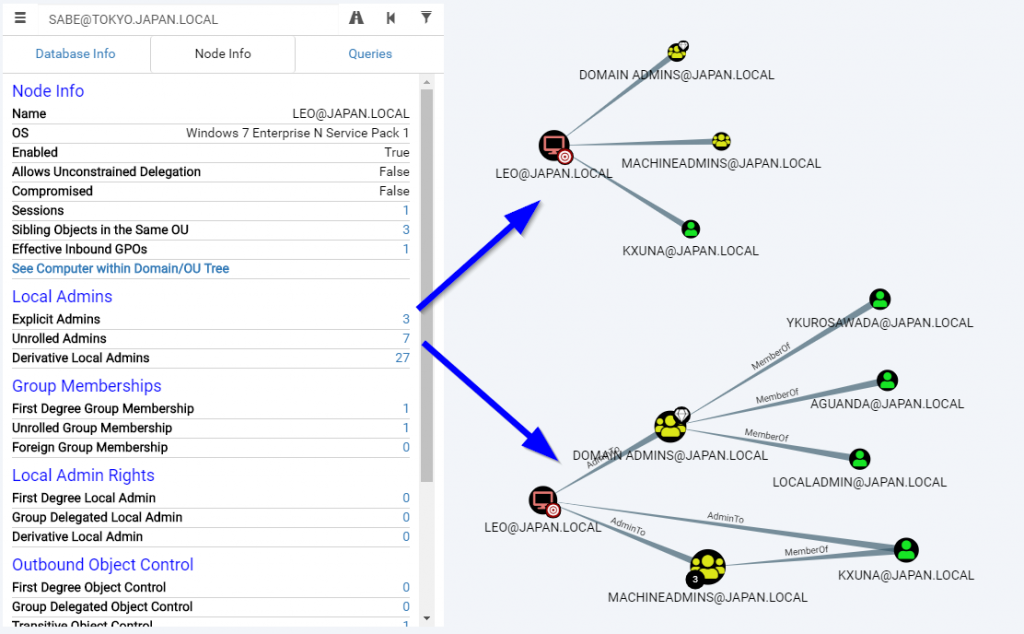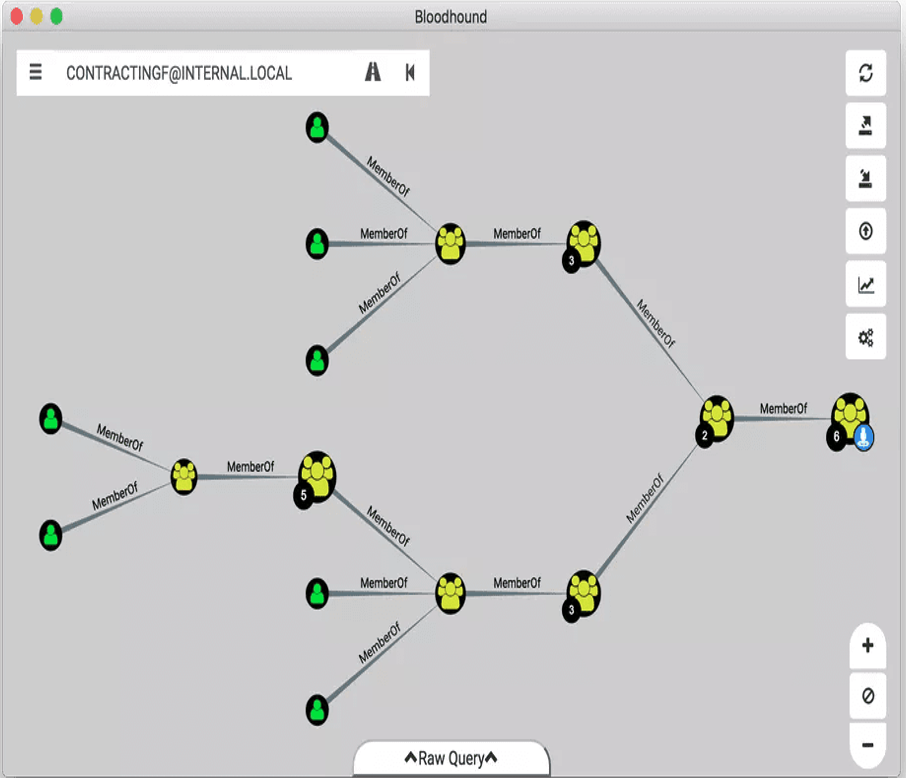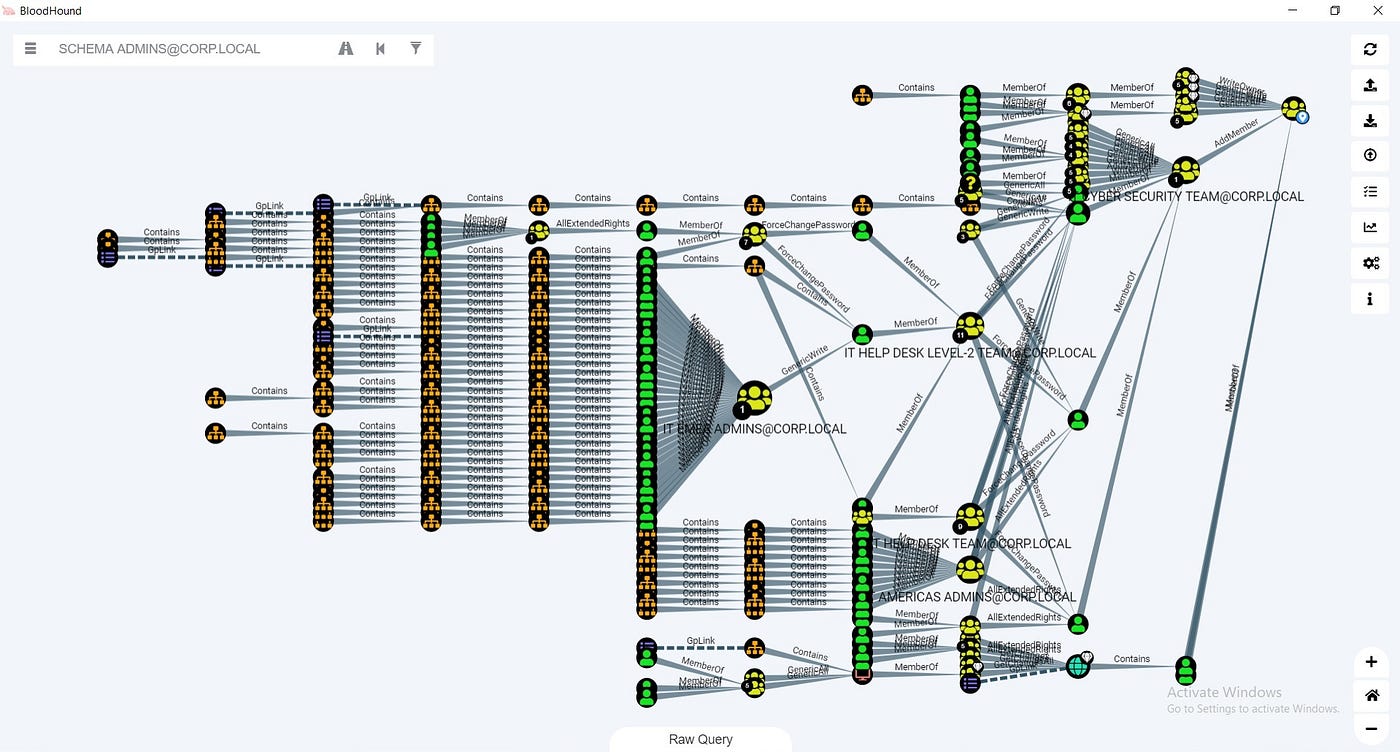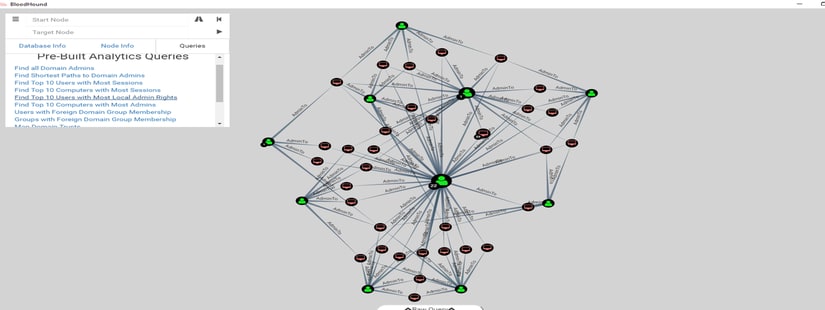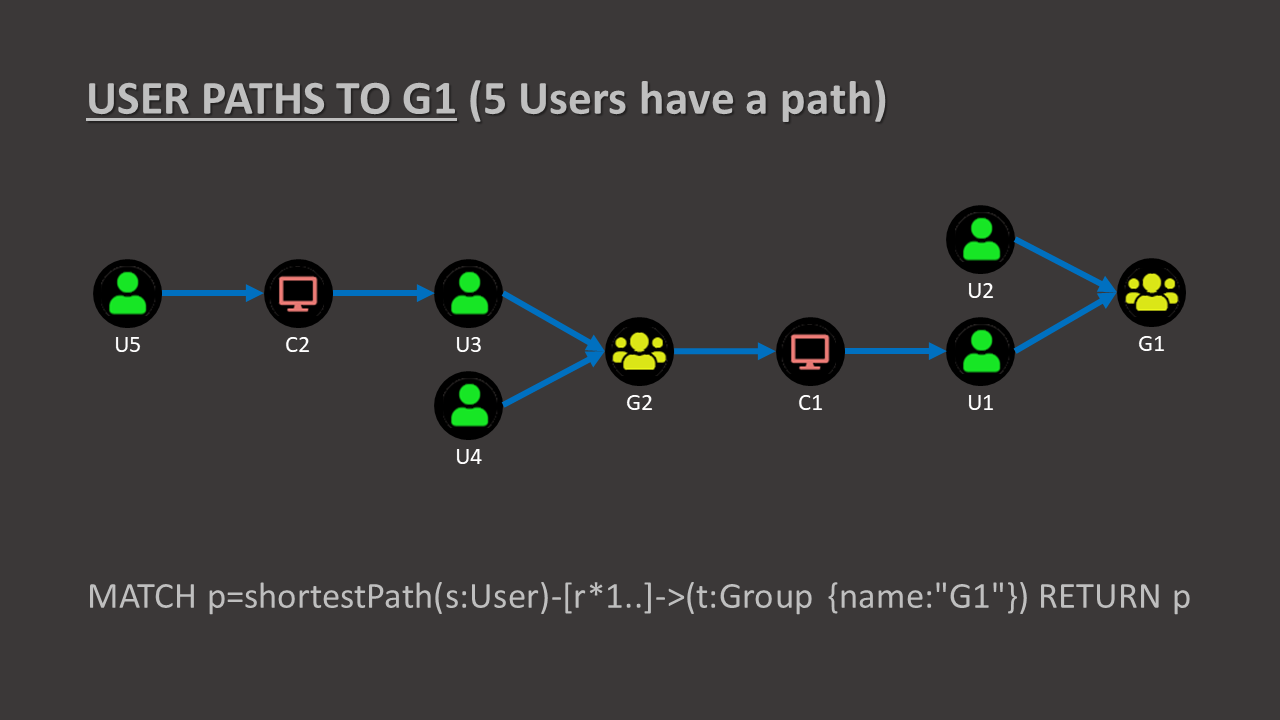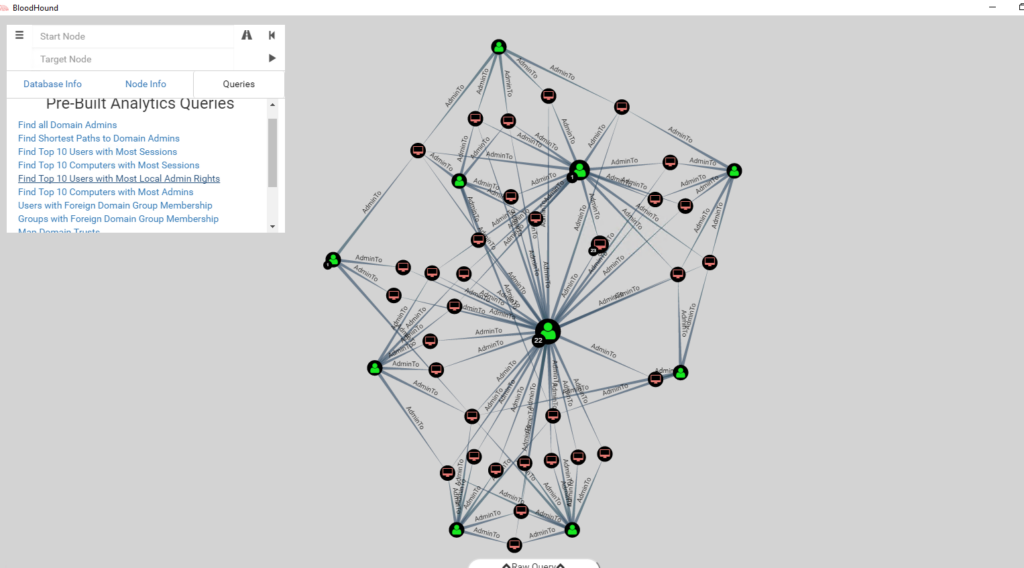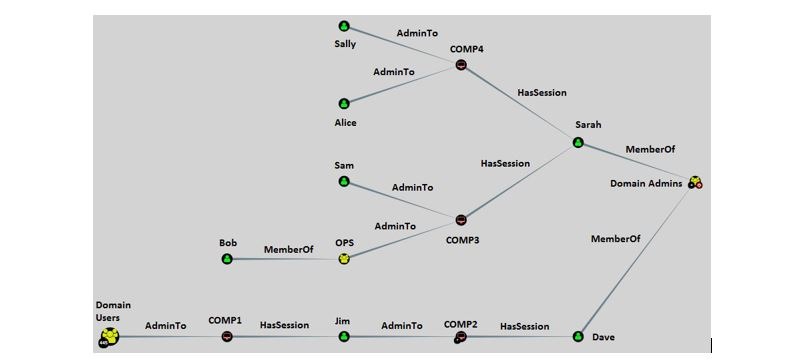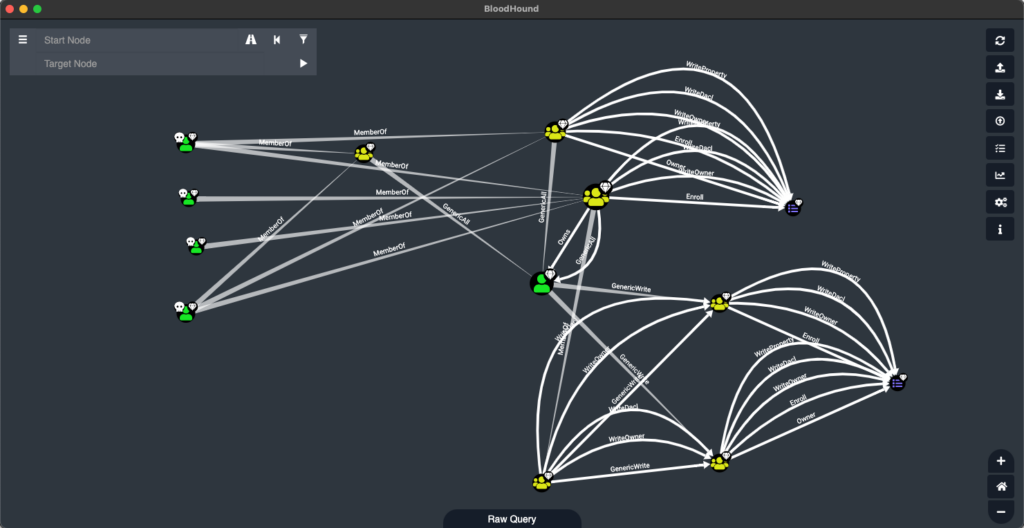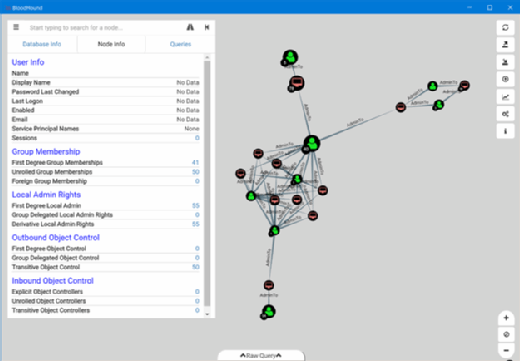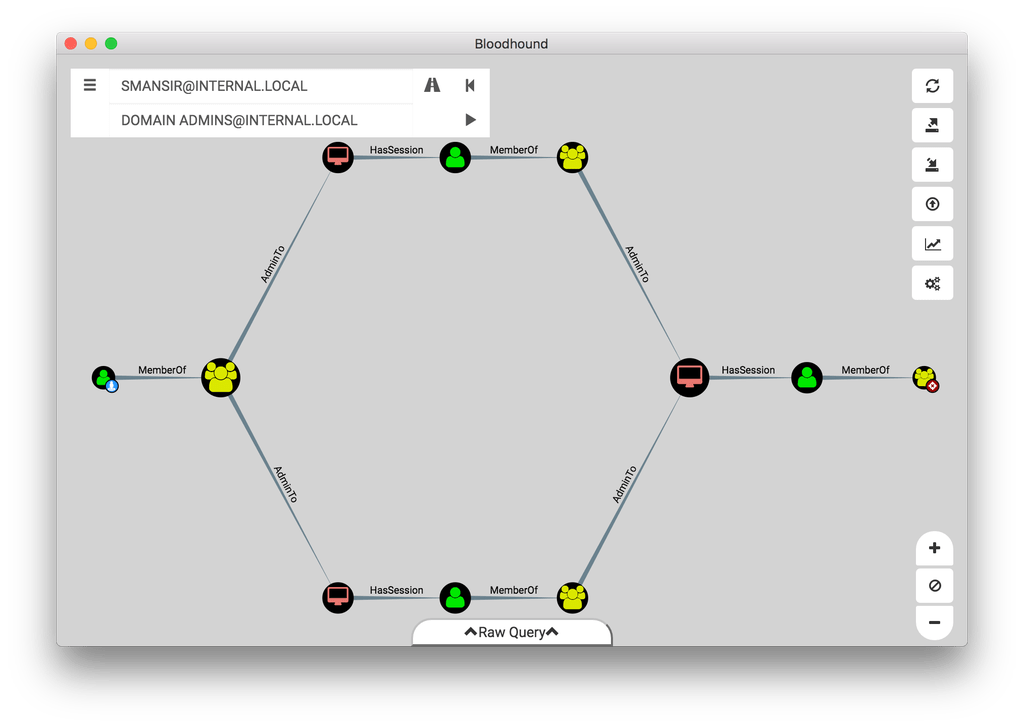
Bloodhound – A Tool For Exploring Active Directory Domain Security - Latest Hacking News | Cyber Security News, Hacking Tools and Penetration Testing Courses
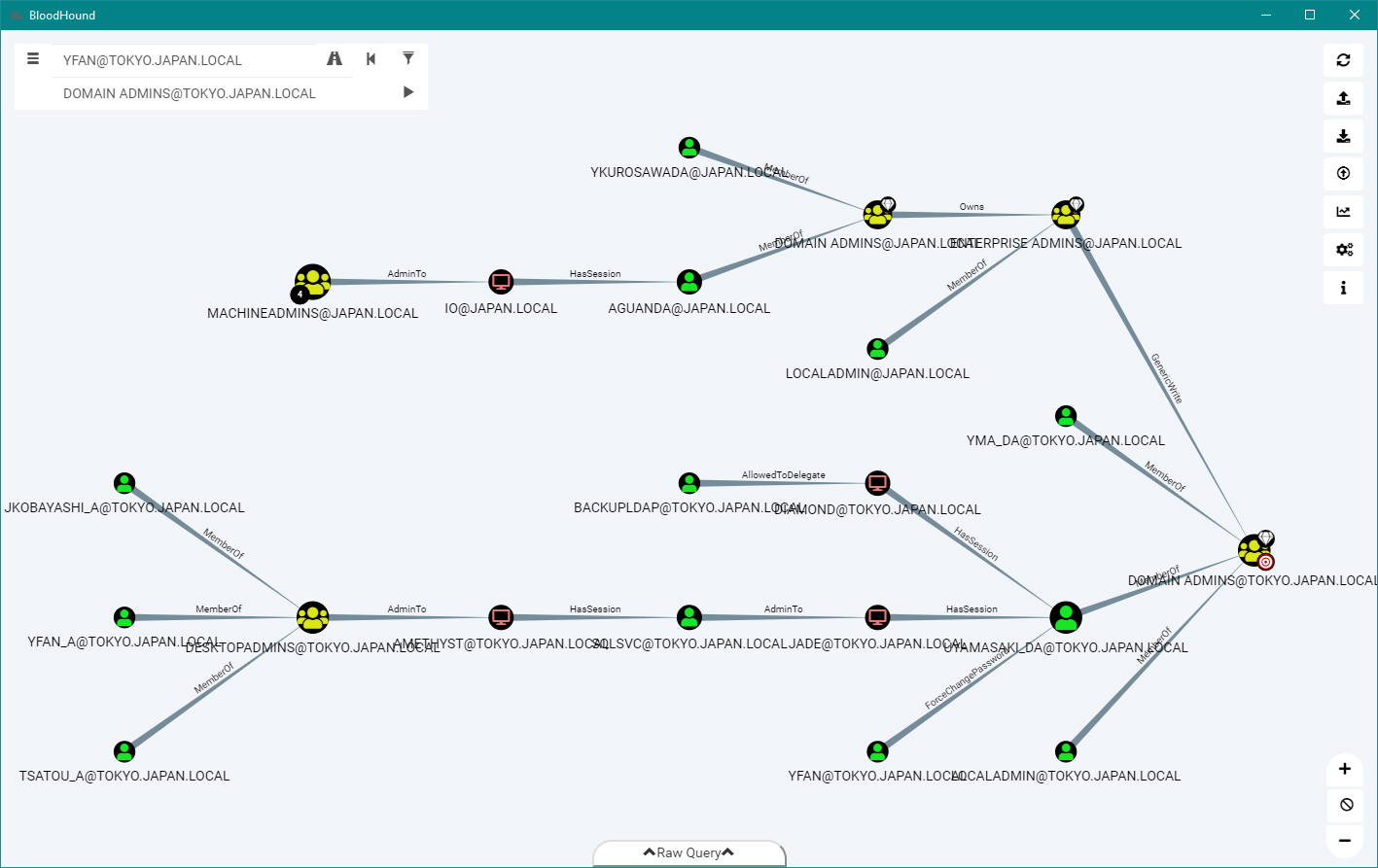
How Attackers Use BloodHound To Get Active Directory Domain Admin Access -- Microsoft Certified Professional Magazine Online